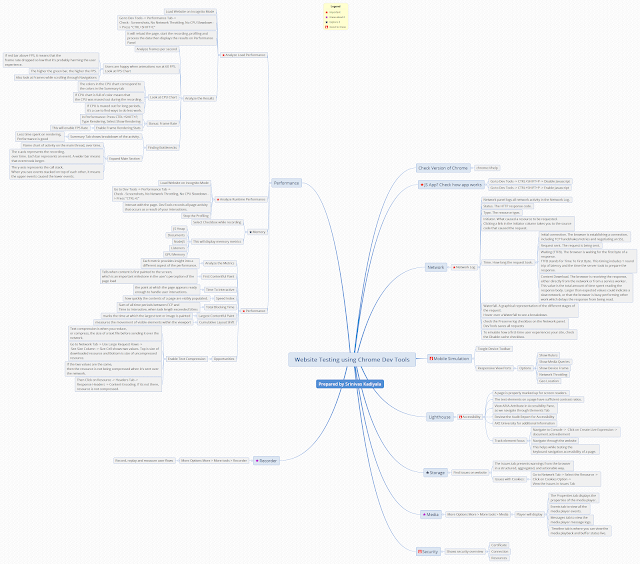
Web Application Security - 2018
Subject: Web Application Security
Topics:
- OWASP - #4: Insecure Cryptographic Storage
- When you register a user, find out how the passwords are stored in application.
- If it is Plain text, then it is leads to security vulnerability.
- Passwords should never be stored in unencrypted format: plain text on server.
- Better way is to store using one-way cryptographic hash of user's password.
- While logging to the application, Password is computed with hash function and compares the hashed password with stored hash password. If both matches, Login is granted.
- Benefits: Only one-way hash, cannot compute the string from hash.
- Hash Functions: SHA-1 , SHA-512 etc.
- More better way to secure is: Adding Salt (Random text) to the password, before computing the hash function. This maximizes the password cryptography.
- Without Salt, when user creates a password as "Hello" and another user creates the same password as "Hello". When they are computed through Hash function. Both Hashed Passwords will be same.

- Reference: Web Application Security - What Testers can do.
- OWASP - #5: Failure to Restrict URL Access
- Keep unauthorized users out of access of modules from UI Navigation and By URL.